So your ISP was really nice and gave you *free* WiFi-enabled router with password-protected encryption and everything? Change the default password. Change it now – because there is nothing safe or secure about it.
The danger of leaving your wireless access point open has been repeatedly reported in the news and countless blog entires. Fortunately, in the interest of protecting their own networks and making their customers feel a little safer, many service providers have been setting up customers with password-protected WiFi-ready routers with built-in firewalls. Awesome, right? Well, sort-of.
As an example, Verizon FiOS customers are given a standard issue router that takes care of everything they need to get a siple home network running and even includes encrypted WiFi protected by 40-bit WEP!
Security-minded people who just finished reading the above sentence have likely done a face-palm at this concept. WEP is broken and has been broken for quite some time. As if that was not enough, 40-bit encryption is the lowest option available and has become trivial to attack and recover if the attacker is in range of the access point. Decryption attacks are possible at even greater distances if the attacker has enough data being broadcast from the access point.
Could this shoddy security deployed on a massive scale to uninformed, yet trusting users get any worse? Sure. When you have to build millions of devices and deploy them efficiently, you pre-configure them exactly the same, or have some sort of predictable pattern that makes them unique – like password selection. This is exactly what the manufacturers and ISPs affected by the vulnerability have done.
The default password on a Verizon FiOS router is based off of the last 5 hex values of the WAN port MAC address. To use my own decommissioned unit as an example, the WAN MAC address is 00:26:62:C0:6A:BF and the default WiFi key is 2662C06ABF. Granted, the WAN MAC address is generally a difficult thing to discover unless you’re standing in front of the router – which is why some helpful people made a database of all the default passwords and used the ESSID of the wireless signal as the lookup key.
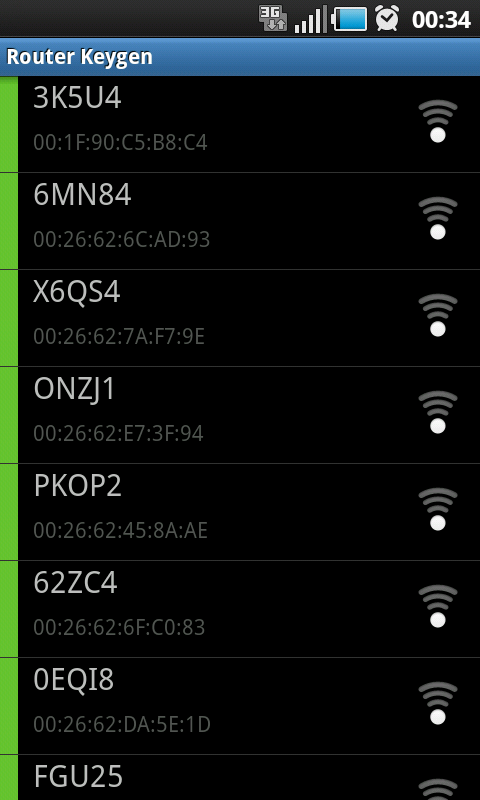
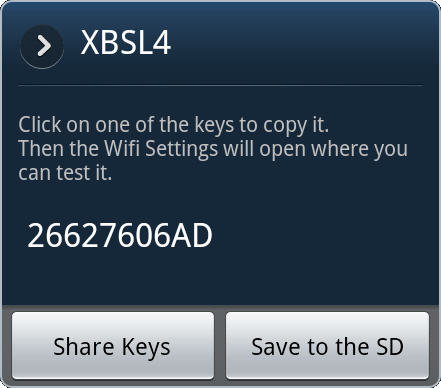
The Router Keygen program is an application for Android phones that uses the phone’s WiFi to scan an area for all wireless access points in range and highlights which points are still set to the default configuration. Selecting a point then tells the user what the password is. The database of all entries takes up about 28MB of storage space, but this is a trivial amount of memory for every Android phone on the market.
Here’s a terrifying and real-world example: I was visiting a friend who lived in a high-rise apartment complex – one of those places where you can see into the balcony windows of about a hundred other apartments across the courtyard. While sitting comfortably in his living room, I turned on Router Keygen to see what would come back. The results were staggering:
The screen-shot to the left is one of three pages of vulnerable access points that I could have accessed and utilised with my phone, laptop, or any wireless device of my choosing. This whole process was completed in the time it took me to unlock my phone and click 1 button. Total wait time for the phone to lookup and start displaying keys was maybe 3 seconds. It’s hard to say with any certainty as my jaw was sitting in my lap from the number of results returned.
Sitting in my friend’s comfy chair, I was looking at a list of about 25 vulnerable networks – any one of which I could have connected to, used their internet connection, other computers, network storage, music and video collections, webcams, and anything else that was open and listening on the network.
The developers of the application were also very thoughtful in giving the ability to lookup passwords manually by ESSID. Running Kismet or similar wireless monitoring software on a laptop, an attacker can quickly and conveniently look up passwords for wireless access points that are out of range for the phone’s antenna, but not for the laptop. If this table on Wikipedia is an accurate representation of reality, someone could access and utilise a vulnerable network hundreds of feet away. Equally as bad, a wireless sniffer could capture and actively decrypt the wireless traffic from thousands of feet away.
Still happy with that free router your ISP gave you? Rather than throwing it in the trash, you should simply fix your security. Here are some helpful tips from the US-CERT Team regarding wireless security with additional comments from me in italics:
- Change default passwords – Most network devices, including wireless access points, are pre-configured with default administrator passwords to simplify setup. These default passwords are easily found online, so they don’t provide any protection. Changing default passwords makes it harder for attackers to take control of the device.
- Restrict access – Only allow authorized users to access your network. Each piece of hardware connected to a network has a MAC address. You can restrict or allow access to your network by filtering MAC addresses. Consult your user documentation to get specific information about enabling these features. There are also several technologies available that require wireless users to authenticate before accessing the network. – A bit of a pain to manage as it requires each device to be added to the authorised list in order to join the network, but if you really want to control what devices are allowed to connect to your network, then this is something you may want to explore.
- Encrypt the data on your network – WEP and WPA both encrypt information on wireless devices. However, WEP has a number of security issues that make it less effective than WPA, so you should specifically look for gear that supports encryption via WPA. Encrypting the data would prevent anyone who might be able to access your network from viewing your data. – And don’t use WEP! Use WPA2. If your device does not support WPA2, then you should get a new device.
- Protect your SSID – To avoid outsiders easily accessing your network, avoid publicizing your SSID. Consult your user documentation to see if you can change the default SSID to make it more difficult to guess. – This tip is suggesting that you avoid broadcasting your SSID, which really doesn’t do much to protect your network as a wireless sniffer will eventually capture some traffic and your SSID will be seen. Changing your SSID to something other than the default will show a party interested in your network that you have taken the time to change the configuration on your devices and getting inside your network will probably be more trouble than they care to invest as there are probably easier targets in range.
- Install a firewall – While it is a good security practice to install a firewall on your network, you should also install a firewall directly on your wireless devices. Attackers who can directly tap into your wireless network may be able to circumvent your network firewall—a host-based firewall will add a layer of protection to the data on your computer. – Although a good practice, the routers I am referring to in this post are also acting as firewalls between the internal network and the Internet. It is possible to have a firewall on a wireless device, but that is beyond the scope of this article and would require a different device than the models I am referring to. If available on your system, you should have the firewalls on all of the computers on your network turned on and only known, trusted systems to connect to each other.
- Maintain anti-virus software – You can reduce the damage attackers may be able to inflict on your network and wireless computer by installing anti-virus software and keeping your virus definitions up to date. Many of these programs also have additional features that may protect against or detect spyware and Trojan horses. – This goes along with the above advice regarding firewalls. Many antivirus programs also come with firewall software built-in.
If you happen to have a neighbor broadcasting that obvious factory-default SSID, please take a moment to tell them how insecure they are and encourage them to change the settings on their router.